Crypto++ Cryptography Library
Crypto++[1] is a free, open-source C++ library for cryptographic schemes originally written by Wei Dai and includes ciphers, message authentication codes, one-way hash functions, public-key cryptosystems, key agreement schemes, and deflate compression[2]. The library is now maintained by several team members and the community. This library offers implementations for well-known and lesser-known schemes and algorithms.
Below is a small list of well-known systems[2].
- Diffie-Hellman Key Agreement
- Advanced Encryption Standard
- RSA Cryptography
- Elliptic Curve Cryptography
- Digital Signature Algorithm
- ElGamal Cryptosystem
- x25519 Key Agreement
- ed25519 Signature Scheme
- ChaCha20 Stream Cipher
List of supported algorithms of Crypto++ version 8.8 as per[1] :
- Authenticated encryption schemes: GCM, CCM, EAX, ChaCha20Poly1305 and XChaCha20Poly1305
- High speed stream ciphers : ChaCha (8/12/20), ChaCha (IETF), Panama, Salsa20, Sosemanuk, XSalsa20, XChaCha20
- AES and AES candidates: AES (Rijndael), RC6, MARS, Twofish, Serpent,CAST-256ARIA
- Other block ciphers: Blowfish, Camellia, CHAM, HIGHT, IDEA, Kalyna (128/256/512), LEA, SEED, RC5, SHACAL-2, SIMON (64/128), Skipjack, SPECK (64/128), Simeck, SM4, Threefish (256/512/1024), Triple-DES (DES-EDE2 and DES-EDE3), TEA, XTEA
- block cipher modes of operation: ECB, CBC, CBC ciphertext stealing (CTS), CFB, OFB, counter mode (CTR), XTS
- Message authentication codes: BLAKE2s, BLAKE2b, CMAC, CBC-MAC, DMAC, GMAC, HMAC, Poly1305, Poly1305 (IETF), SipHash, Two-Track-MAC, VMAC
- Hash functions: BLAKE2s, BLAKE2b, Keccack (F1600), LSH (256/512), SHA-1, SHA-2 (224/256/384/512), SHA-3 (224/256), SHA-3 (384/512), SHAKE (128/256), SipHash, SM3, Tiger, RIPEMD (128/160/256/320), WHIRLPOOL
- Public-key cryptography: RSA, DSA, Deterministic DSA, ElGamal, Nyberg-Rueppel (NR), Rabin-Williams (RW), LUC, LUCELG, EC-based German Digital Signature (ECGDSA),DLIES (variants of DHAES), ESIGN
- Padding schemes for public-key: PKCS#1 v2.0, OAEP, PSS, PSSR, IEEE P1363 systems EMSA2 and EMSA5
- Key agreement schemes: Diffie-Hellman (DH), Unified Diffie-Hellman (DH2), Menezes-Qu-Vanstone (MQV), Hashed MQV (HMQV), Fully Hashed MQV (FHMQV), LUCDIF, XTR-DH
- Elliptic curve cryptography: ECDSA, Deterministic ECDSA, ed25519, ECNR, ECIES, ECDH, ECMQV, x25519
- Insecure or obsolescent algorithms retained for backwards compatibility and historical value: MD2, MD4, MD5, Panama Hash, DES, ARC4, SEAL 3.0, WAKE-OFB, DESX (DES-XEX3), RC2, SAFER, 3-WAY, GOST, SHARK, CAST-128, Square
The list of other features of Crypto++ as presented in [1]:
- Pseudo random number generators (PRNG): ANSI X9.17 appendix C, RandomPool, DARN, VIA Padlock, RDRAND, RDSEED, NIST Hash and HMAC DRBGs
- Password based key derivation functions: PBKDF1 and PBKDF2 from PKCS #5,PBKDF from PKCS #12 appendix B, HKDF from RFC 5869, Scrypt from RFC 7914
- Shamir’s secret sharing scheme and Rabin’s information dispersal algorithm
(IDA) - Fast multi-precision integer (bignum) and polynomial operations
- Finite field arithmetics, including GF(p) and GF(2^n)
- Prime number generation and verification
- Useful non-cryptographic algorithms+ DEFLATE (RFC 1951) compression/decompression with gzip (RFC 1952) and
zlib (RFC 1950) format support
+ Hex, base-32, base-64, URL safe base-64 encoding and decoding
+ 32-bit CRC, CRC-C and Adler32 checksum - class wrappers for these platform and operating system features (optional):
+ high resolution timers on Windows, Unix, and Mac OS
+ /dev/random, /dev/urandom, /dev/srandom
+ Microsoft’s CryptGenRandom or BCryptGenRandom on Windows - A high level interface for most of the above, using a filter/pipeline
metaphor - Benchmarks and validation testing
- x86, x64 (x86-64), x32 (ILP32), ARM-32, Aarch32, Aarch64 and Power8 in-core code for the commonly used algorithms
+ run-time CPU feature detection and code selection
+ supports GCC-style and MSVC-style inline assembly, and MASM for x64
+ x86, x64 (x86-64), x32 provides MMX, SSE2, and SSE4 implementations
+ ARM-32, Aarch32 and Aarch64 provides NEON, ASIMD and ARMv8 implementations
+ Power8 provides in-core AES using NX Crypto Acceleration
One may try this procedure on any Linux system. But, here we use chrooted Debin 10 Buster System which was virtually installed on a Debian 11 Bullseye host (yes Debian 10 on Debian 11 for safety reasons). Those who do not know what is chroot based virtualization then may read the following article[6]:
Installing ns3.35 in Debian 10 chroot Jail Under Debian 11 Host OS or any Version of Linux Host
Note: In fact, the ns-3 installation part of that article is not necessary for proceeding with this tutorial. So, to follow this tutorial, just installing a Linux system is sufficient or you may use one if you are already having it.
A. Installing Crypto++ from Binary version
Install the binary version of crypto++ (libcryptopp) on Ubuntu
$sudo apt-get install libcrypto++-dev libcrypto++-doc libcrypto++-utils
This will install crypto++ library and its development supports under Linux file system.
Instead of using the binary version, you can download and compile crypto++ from source version. The next section explains this.
B. Installing Crypto++ from the Source version
Step 1: Downloading Crypto++
One may download source and binary versions of Crypto++ from [6] or download the source version from [1].
In this procedure, I used the source version of Crypto++ version from [1].
$ git clone https://github.com/weidai11/cryptopp
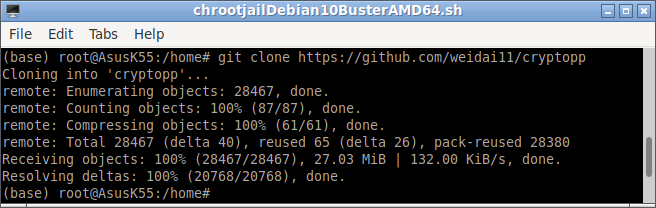
Step 2: Compiling Crypto++
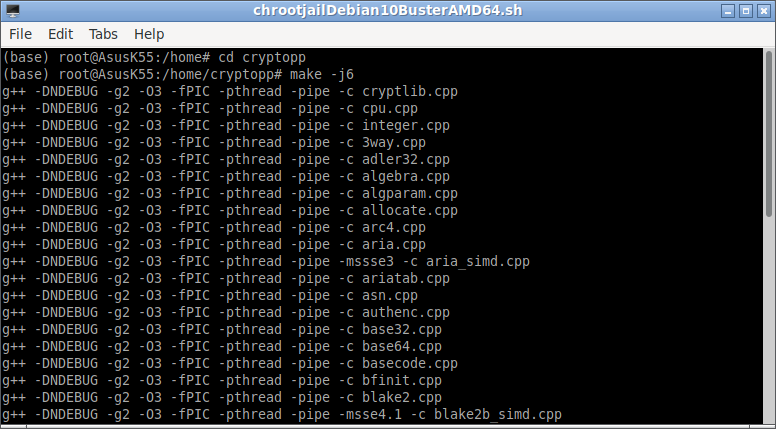
After downloading the latest version of Crypto++ from [1], we may compile it as follows:
$ make
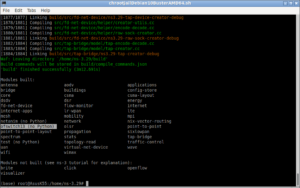
The above command will compile Crypto++ library.
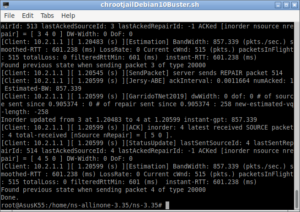
The following screenshot shows the start of the build process :
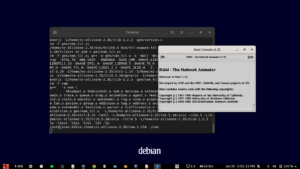
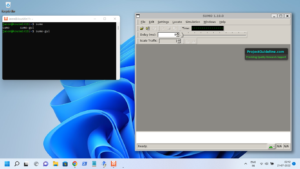
You will see the following screen at the successful end of the test process.
For that you have to do the following:
Now we are ready to use the Crypto++ library.
Step 4: Testing the good working of Crypto++
After installing Crypto++, before trying to use it with ns-3, we have to test the good working status of the library installation by using it in a simple CPP program.
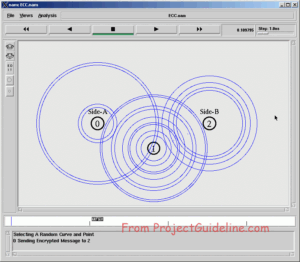
The following “ecctest.cpp” is one such sample program provided at [7]. It will perform curve operations directly. The j following code from[7] shows you how to exponentiate, multiply and add using the lower-level primitives over secp256r1.
#include "integer.h" #include "eccrypto.h" #include "osrng.h" #include "oids.h" #include#include int main(int argc, char* argv[]) { using namespace CryptoPP; typedef DL_GroupParameters_EC GroupParameters; typedef DL_GroupParameters_EC ::Element Element; AutoSeededRandomPool prng; GroupParameters group; group.Initialize(ASN1::secp256r1()); // private key Integer x(prng, Integer::One(), group.GetMaxExponent()); std::cout << "Private exponent:" << std::endl; std::cout << " " << std::hex << x << std::endl; // public key Element y = group.ExponentiateBase(x); std::cout << "Public element:" << std::endl; std::cout << " " << std::hex << y.x << std::endl; std::cout << " " << std::hex << y.y << std::endl; // element addition Element u = group.GetCurve().Add(y, ECP::Point(2,3)); std::cout << "Add:" << std::endl; std::cout << " " << std::hex << u.x << std::endl; std::cout << " " << std::hex << u.y << std::endl; // scalar multiplication Element v = group.GetCurve().ScalarMultiply(u, Integer::Two()); std::cout << "Mult:" << std::endl; std::cout << " " << std::hex << v.x << std::endl; std::cout << " " << std::hex << v.y << std::endl; return 0; }
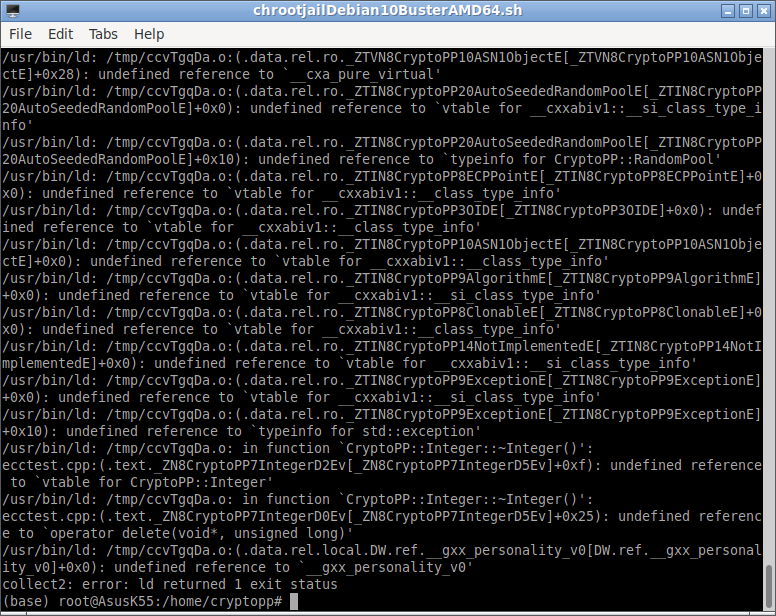
If you compile the code using gcc or g++, then probably you may end up with an error like the following one:
To successfully run the code, you have to do the following :
Now we can run the compiled ecc test program.
It will produce an output like this:
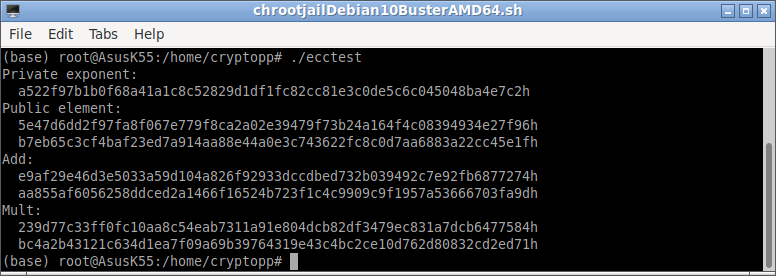
The above output shows the successful run of the ecc example program.
Conclusion
This article explains the way of installing the Crypto++ library under Linux using the source version as well as the binary version of that library. After installing this library we can use it in our programs to do cryptography-related operations. Even it is possible to do the modification in the source version of the library for doing new research work related to cryptography.
The following article[7] explains the way of compiling ns-3 along with Crypto++ library and using cryptographic function of this library with ns-3 simulations.
Secrets of Using Cryptography in ns-3 using Crypto++ Library
- https://github.com/weidai11/cryptopp
- https://www.cryptopp.com/wiki/Main_Page
- https://www.cryptopp.com/wiki/Linux
- https://www.cryptopp.com/
- https://www.cryptopp.com/wiki/Elliptic_Curve_Cryptography
- https://www.projectguideline.com/installing-ns3-35-in-debian-10-chroot-jail-under-debian-11-host-os-or-any-version-of-linux-host/
- https://www.projectguideline.com/secrets-of-using-cryptography-in-ns-3-using-crypto-library/

 Discuss Through WhatsApp
Discuss Through WhatsApp